Another amazing social engineering tool is Ghost Phisher. It provides a number of easy-to-use utilities for creating social engineering attacks very quickly with its graphical user interface (GUI).
To get started with Ghost Phisher, follow these steps:
- On Kali Linux, click Applications | Social Engineering Tools | Ghost Phisher.
- Once the tool is open, you'll be presented with the options of the main tab, that is, Fake Access Point:

Once your wireless network adapter is connected to your Kali Linux machine, go to the wireless interface in the menu and customize the Fake Access Point settings as per your preferences.
- To create a rogue DHCP server, simply select the Fake DHCP Server tab and add the necessary information, as shown in the following screenshot:

- The Session Hijacking tab allows you to perform an MITM attack and capture live sessions:

Ensure that you set the default gateway of your network before starting the session hijacking attack on Ghost Phisher.
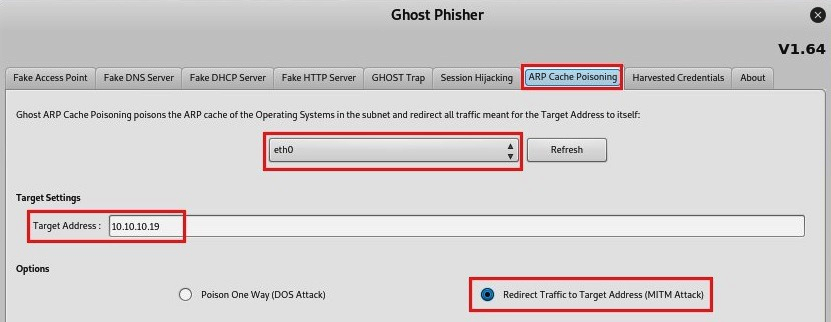
- Similar to arpspoof, there's a built-in ARP spoofing tool for quickly enabling an MITM attack:
Ghost Phisher provides many functions to a penetration tester through a simple and easy-to-use interface; there's even an additional tab called Harvested Credentials that displays all the usernames and passwords that were captured during any attacks that had been launched.
