The Data Transfer Length
Behavior Permitted by the Spec
When an IO read or write transaction is initiated, the data transfer length is output by the Request Agent in request packet B (see Table 49-8 on page 1219). The spec permits IO data transfer lengths of:
A qword or less. Any combination of byte enables are valid, including none.
Two full qwords. All byte enables must be asserted in request packet B.
Four full qwords. All byte enables must be asserted in request packet B.
Eight full qwords. All byte enables must be asserted in request packet B.
On a 0-byte read, the response must be the no data response (unless DEFER# is asserted by the Response Agent, indicating that it intends to retry or defer the transaction).
On a 0-byte write, the Response Agent must assert TRDY#, but the Request Agent must not assert DBSY# or DRDY# in response. Note that the author doesn't know why an agent would initiate a 0-byte IO transaction. IA32 processors are incapable of doing this.
How the Pentium® 4 Processor Operates
The Pentium® 4 processor only performs IO read and write transactions due to the execution of IO read (IN or INS) or write (OUT or OUTS) instructions. The programmer may only specify the AL, AX, or EAX register as the target or source register for the read or write. This restricts the transfers to:
a single byte.
two contiguous bytes.
four contiguous bytes.
This means that, at most, the transfer length will always be less than a qword and, at a maximum, four contiguous byte enables will be asserted. If the accessed data crosses a dword address boundary, the processor will behave as follows:
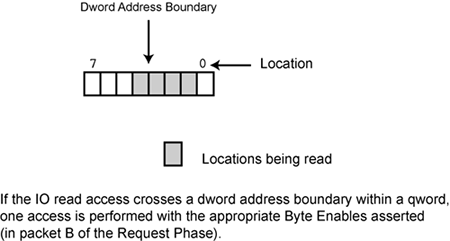
If the transaction is an IO read and the access crosses the dword boundary within a qword (see Figure 53-2 on page 1298), one access is performed with the appropriate byte enables asserted.
Figure 53-2. An IO Read that Crosses a Dword Address Boundary
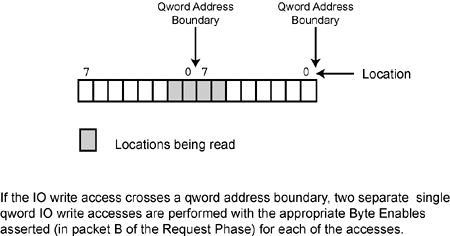
If the transaction is an IO read and the access crosses a qword boundary (see Figure 53-3 on page 1299), two separate single-qword accesses are performed with the appropriate byte enables asserted.
Figure 53-3. An IO Read that Crosses a Qword Address Boundary
If the transaction is an IO write and the access crosses the dword boundary within a qword (see Figure 53-4 on page 1299), two accesses are performed with the appropriate byte enables asserted.
Figure 53-4. An IO Write that Crosses a Dword Address Boundary

If the transaction is an IO write and the access crosses a qword boundary (see Figure 53-5 on page 1300), two separate single-qword accesses are performed with the appropriate byte enables asserted.
Figure 53-5. An IO Write that Crosses a Dword Address Boundary

